
Data Models (ADBMS)
Mr. Vivek Sharma, Assistant Professor, Biyani Girls College explained about Data Models. It is a way which is useful to store information or records in the Database. www.gurukpo.com, www.biyanicolleges.org <iframe width=”560″ …

Mr. Vivek Sharma, Assistant Professor, Biyani Girls College explained about Data Models. It is a way which is useful to store information or records in the Database. www.gurukpo.com, www.biyanicolleges.org <iframe width=”560″ …

Dr Preetpal Kaur, Assistant Professor, Biyani girls College explained about the theory of cell and difference between prokaryotic and eukaryotic. www.gurukpo.com, www.biyanicolleges.org
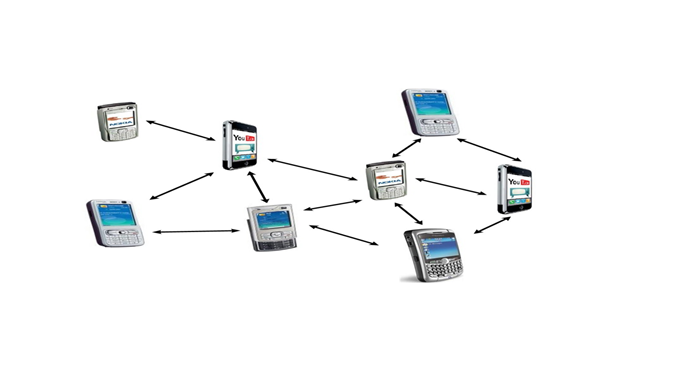
A Mobile Ad hoc Network (MANET) is a self governing network of mobile nodes connected through wireless links. Mobile ad hoc networks (MANET) are infrastructure less networks, dynamically formed by an …

Ms. Kanchan Sharma, Assistant Professor, Biyani girls College explained about Eloborated LAC-Operon and its functioning, enzyme activity and control mechenisms by catabolic repression. www.gurukpo.com, www.biyanicolleges.org

Dr. Preetpal Kaur Assistant Professor, Biyani Girls College explained about structure origin & function of Golgi body. www.gurukpo.com, www.biyanicolleges.org
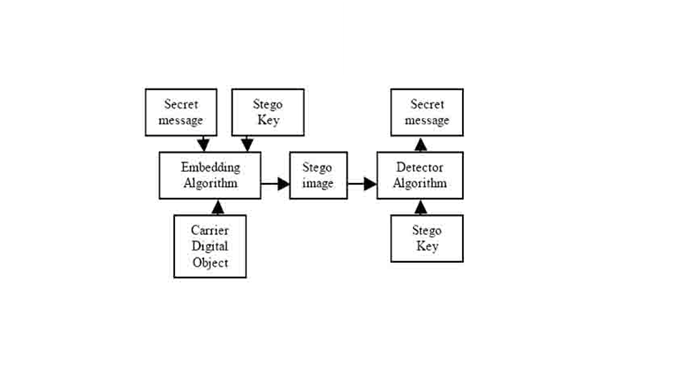
The word steganography comes from the Greek word Steganos, which mean covered or secret and graphy means writing or drawing. Therefore, steganography means, literally, covered writing. Steganography is the art and …

It is part of lecture presented by Shalini Singh, Lecturer at Biyani Girls College on behalf of Guru KPO. This lecture discusses the major macroeconomic concern i.e. inflation, output level and …

Previous week the HEAT-hosted summer educate on FHE and multi-linear map took place. On the final day we learned about in distinguish ability obfuscation from the eminent cryptographer Amit Sahai. The …

It is part of lecture presented by Abhishek Baldwa Asst. Prof. at Biyani nGirls College on behalf of Guru KPO. This lecture discusses the insolation and heat budget of the Earth. …